Firewall/en: Unterschied zwischen den Versionen
Keine Bearbeitungszusammenfassung |
Keine Bearbeitungszusammenfassung |
||
| Zeile 20: | Zeile 20: | ||
==VLAN Requirements== | ==VLAN Requirements== | ||
Every virtual | Every virtual Securepoint UTM has 2x virtual network interfaces.<br> | ||
One of them communicates with the Internet, the other communicates with the systems in the package.<br> | One of them communicates with the Internet, the other communicates with the systems in the package.<br> | ||
Since a Hyper-V VM can have a maximum of 8x network cards attached, we can provide a maximum of 6x additional VLANs.<br> | Since a Hyper-V VM can have a maximum of 8x network cards attached, we can provide a maximum of 6x additional VLANs.<br> | ||
Version vom 3. Juli 2024, 09:01 Uhr
Private Cloud Strategy
Basically, every private cloud package from the TERRA CLOUD is delivered with a virtual Securepoint UTM appliance.
This starter guide serves as the basis for setting up a VPN tunnel and accessing the firewall's web interface.
Requirements for access
OpenVPN Client:
- Securepoint VPN Client - Download Link
- other OpenVPN client
- OpenVPN Client for MacOS - click here
VPN configuration file:
The VPN data for administrator access can be found in the Cloud Center below the respective order within the service information, see also Service-Information.
The point "to the download area" takes you to a central share in Terra Drive, where all your VPN data for the booked virtual environments in the Terra Cloud is located. The prerequisite for this is the access data for your Drive NFR account.
Please note that the central share only contains the VPN data of the environments that you have booked in the Terra Cloud Center.
VLAN Requirements
Every virtual Securepoint UTM has 2x virtual network interfaces.
One of them communicates with the Internet, the other communicates with the systems in the package.
Since a Hyper-V VM can have a maximum of 8x network cards attached, we can provide a maximum of 6x additional VLANs.
Connect to the firewall
An existing VPN tunnel is required for the connection to the firewall.
Before establishing the connection, please check whether the standard port 1194 is enabled for VPN connections on your local firewall.
If port 1194 is blocked, establishing the VPN tunnel will fail.
Initial setup of the VPN connection in the Securepoint VPN Client
- Install the respective VPN client, in this example we are assuming the Securepoint VPN client.
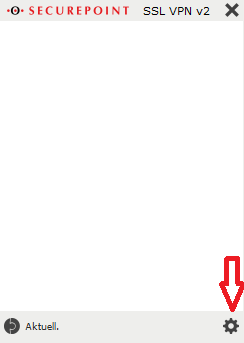
- Open the VPN client and click the gear at the bottom right to open the settings menu..
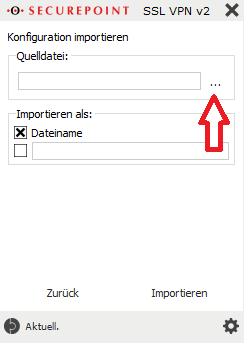
- In the context menu under Source file, click on the three dots to select the source file that was previously downloaded from the Cloud Portal.
- Select the opvn file from the previously extracted zip file and click “Import”.
- Optionally, the configuration can be assigned a name under “Import as:” under which the configuration will later be visible in the VPN client.
- Use the arrow button to start establishing the VPN connection
The required initial access data is:
User: ssluser-admin
Password: ChanTroFar93!
Connection to the firewall web interface
After the VPN connection has been successfully established, access the following address in any browser:
https://<firewall IP address>:11115
The IP address of the firewall was assigned by you when ordering the environment and can be accessed subsequently in the Cloud Center
can be viewed below the respective order within the service information, see also Service Information.

The required initial access data is:
User: fwadmin
Password: Terra001
Initial access to the firewall web interface
Note:
The WebGUI has changed visually since firmware version 12.6.2.
However, with a few exceptions, all points are still called the same, so you can continue to follow all the steps using the following instructions.
The first time you open the firewall web interface, a few things need to be done:
Assign firewall name
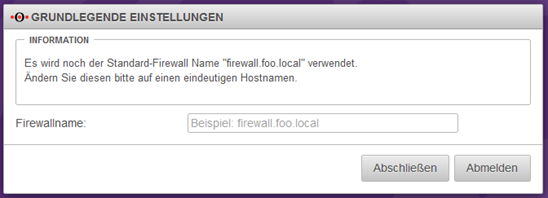
Please enter a firewall name, which must correspond to an FQDN, e.g. myfirewall.local.
The firewall name must not contain any umlauts, special characters or capital letters.
Then click on the Complete button.
Firmware Update
Depending on the preinstalled firmware version, you will receive a message that a newer firmware is available.
In this example we assume that version 11.8.9 is preinstalled.
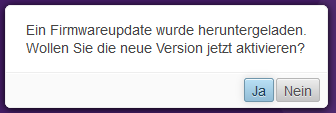
This query should be answered with Yes when the environment is commissioned for the first time.
You will then receive a view of the available new firmware, which will be imported using the “Start test run” button.
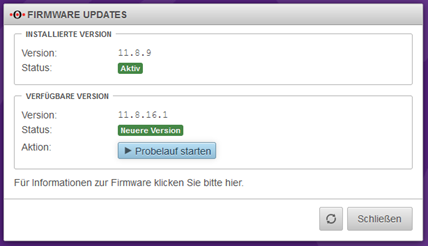
In order to use the new firmware, several license agreements must be checked and accepted.
Finally, a restart must be carried out. This can take up to 5 minutes.
You can follow the restart via the console connection via the Technical Center (https://manage.terracloud.de).
After the firewall has successfully restarted and you have logged in again, the new firmware must be confirmed as the new standard firmware.
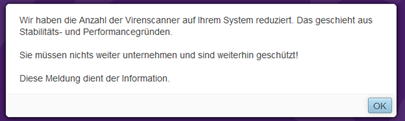
Confirm virus scanner message
If you have booked the firewall with only one vCore, you will receive a message that the number of virus scanners on the firewall has been reduced for stability and performance reasons.
This message is normal and needs to be confirmed.
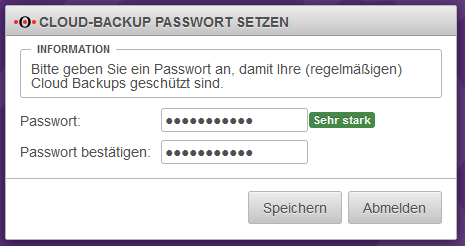
Set cloud backup password
Please enter a password to back up your firewall configuration in the Securepoint cloud.
This gives you the opportunity to import the firewall configuration from the Securepoint Cloud after reinstalling the firewall.
Your firewall will then be completely set up.
Change of initial passwords
We recommend changing the initial passwords after the handover.
- In the firewall interface, open the menu item Authentication --> Users
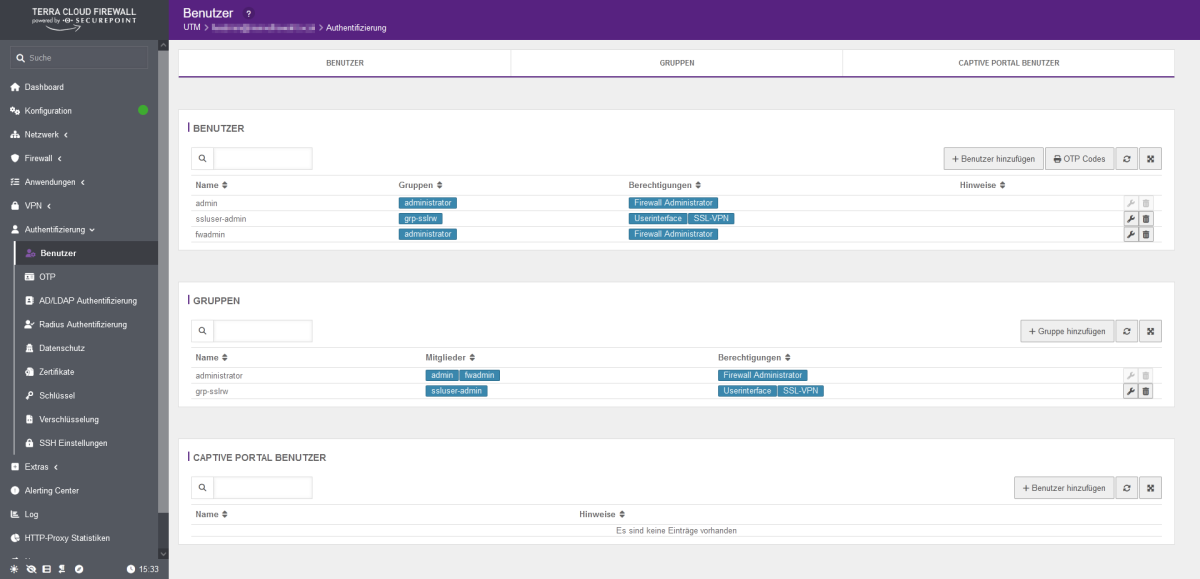
- Click on the configuration symbol (wrench) behind the respective user and enter the new password in the Password and Confirm password fields.
- Finally, click on the save symbol at the top right.
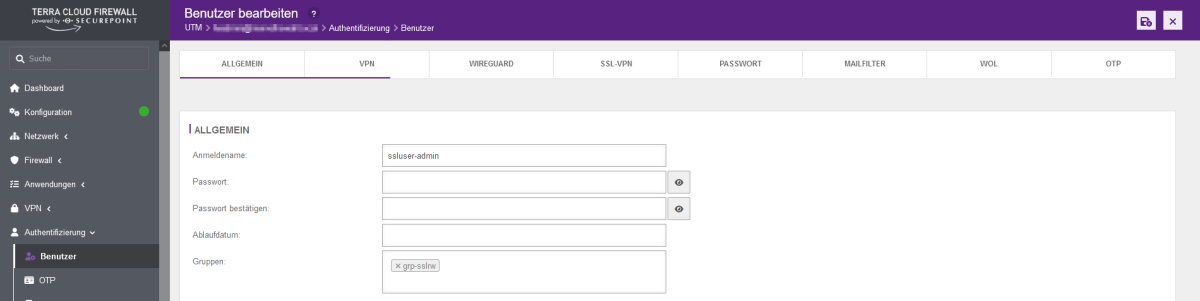
You cannot change the user "admin".
This is an administrative account that is only used in the background for the firewall services.
Instructions and information on configuring the firewall can be found at:
http://wiki.securepoint.de/index.php/Howtos-V11
Email protection: spam filter with anti-virus package (optional)
Protection is implemented directly on the firewall included in the cloud environment.
The following options can be set:
- https://wiki.securepoint.de/UTM/APP/Mailfilter
- https://wiki.securepoint.de/UTM/APP/Mailrelay-Best_Practice
Internet protection: Content filter with anti-virus package (optional)
Internet protection is implemented on the cloud firewall in your cloud environment. The following options can be set:
Change of internal IP address
To change the internal IP address without losing access to the firewall,
first the new IP address must be added, the VPN settings adjusted and only then the old IP address deleted.
- First the network object "Internal-Interface" is adjusted. To do this, open the packet filter under the "Firewall" tab.
- Under "Network objects" you will find the "internal-interface" object. Open the settings of the network object by clicking on the "wrench".
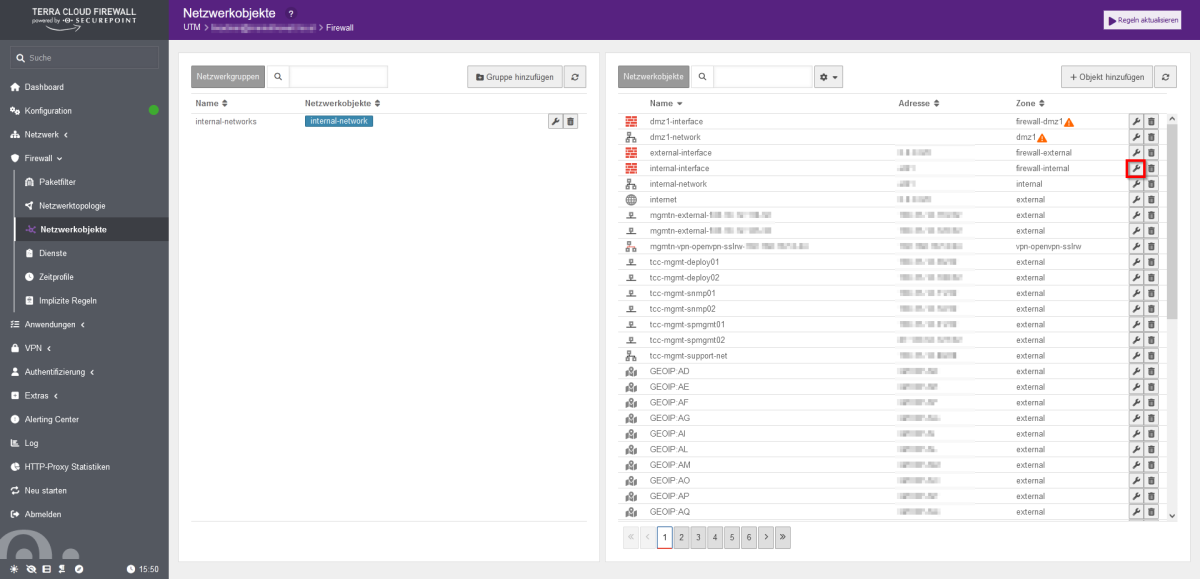
- Regardless of the initial state, select “eth1” here under “Interface”
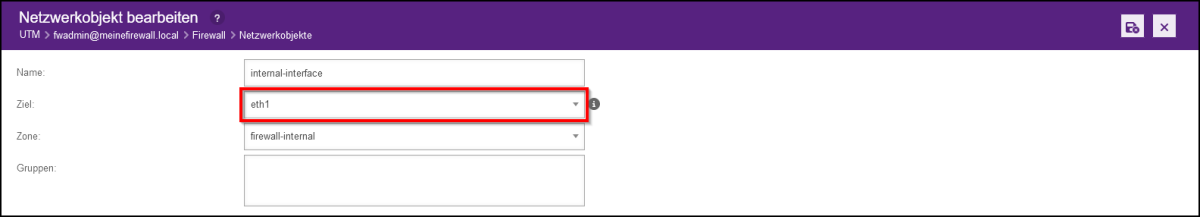
Note: In the newer firewall version, the interface field was renamed target and eth1 was renamed lan2.
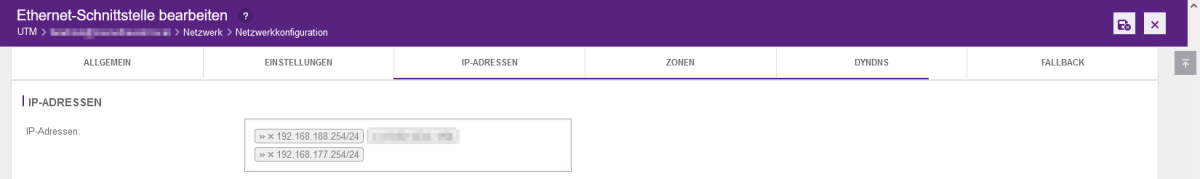
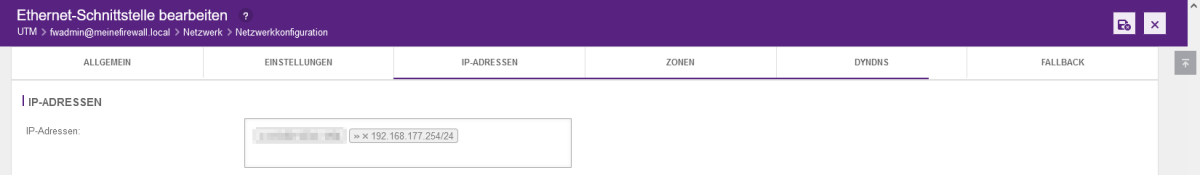
- The new IP network is then assigned. Open the network configuration in the firewall web interface under the “Network” tab.
- On the right side, click on the “wrench” of eth1 for the configuration.
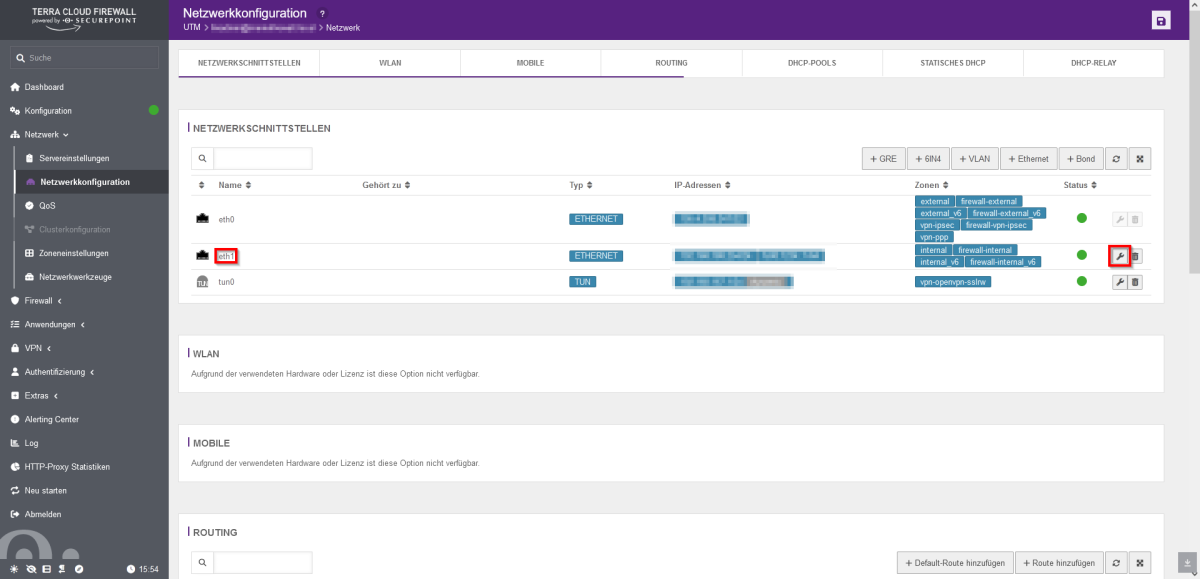
- Add the new IP address under the “IP addresses” tab.
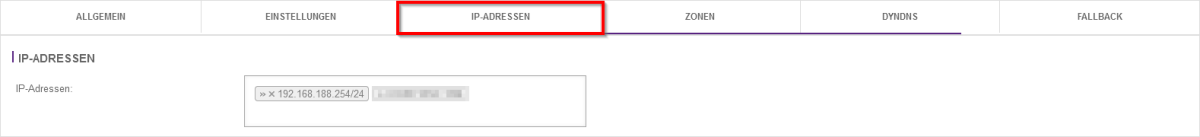

- If you only want to change the host address, it is sufficient to enter the new address here, delete the old address using the small x and complete this by clicking on the "Save" button.
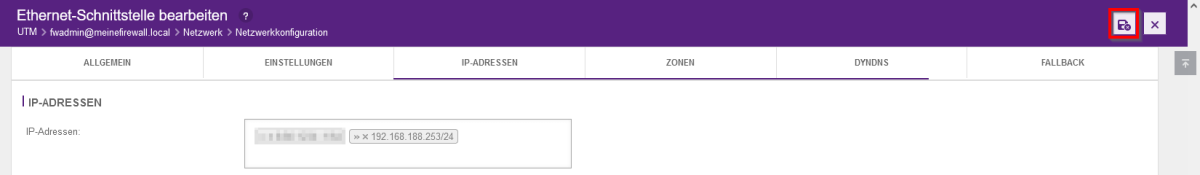
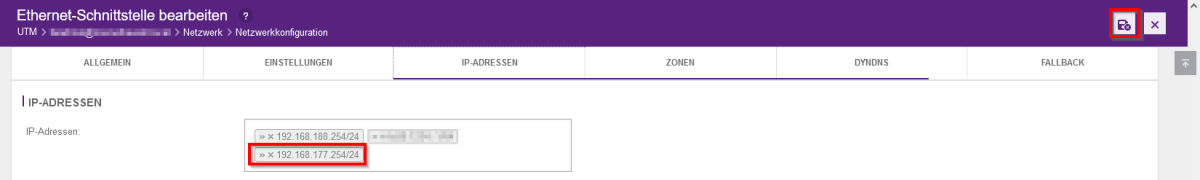
- However, if you want to change the subnet, you must make further settings for the VPN tunnel before deleting the old IP address.
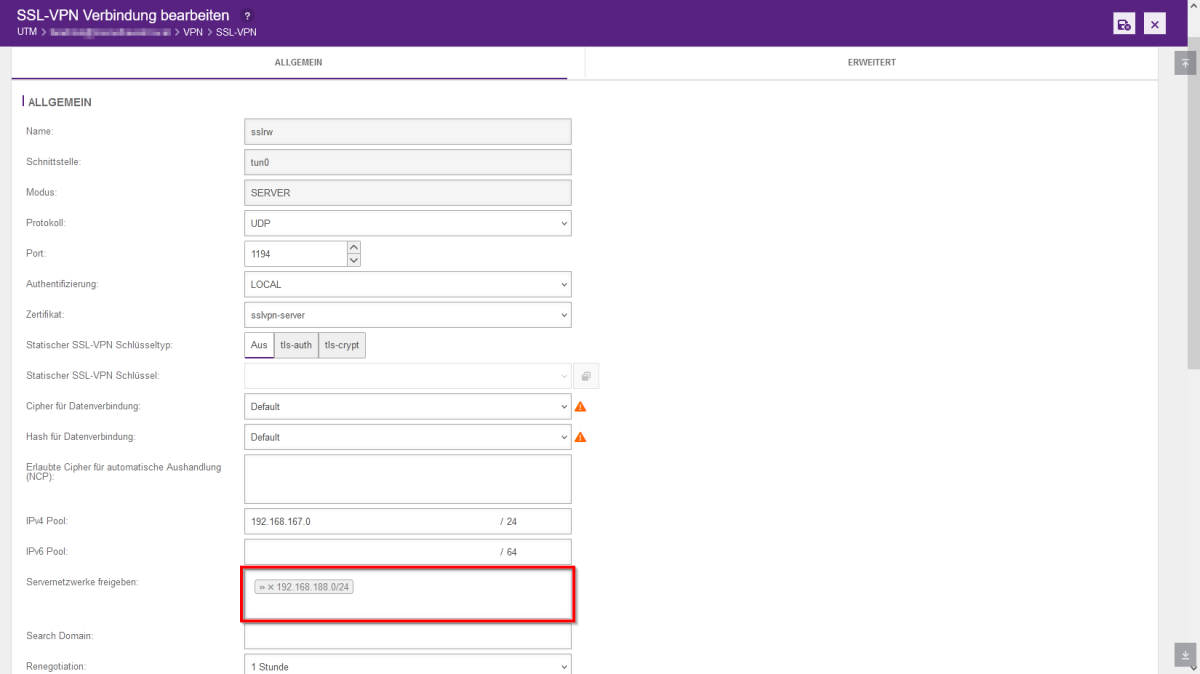
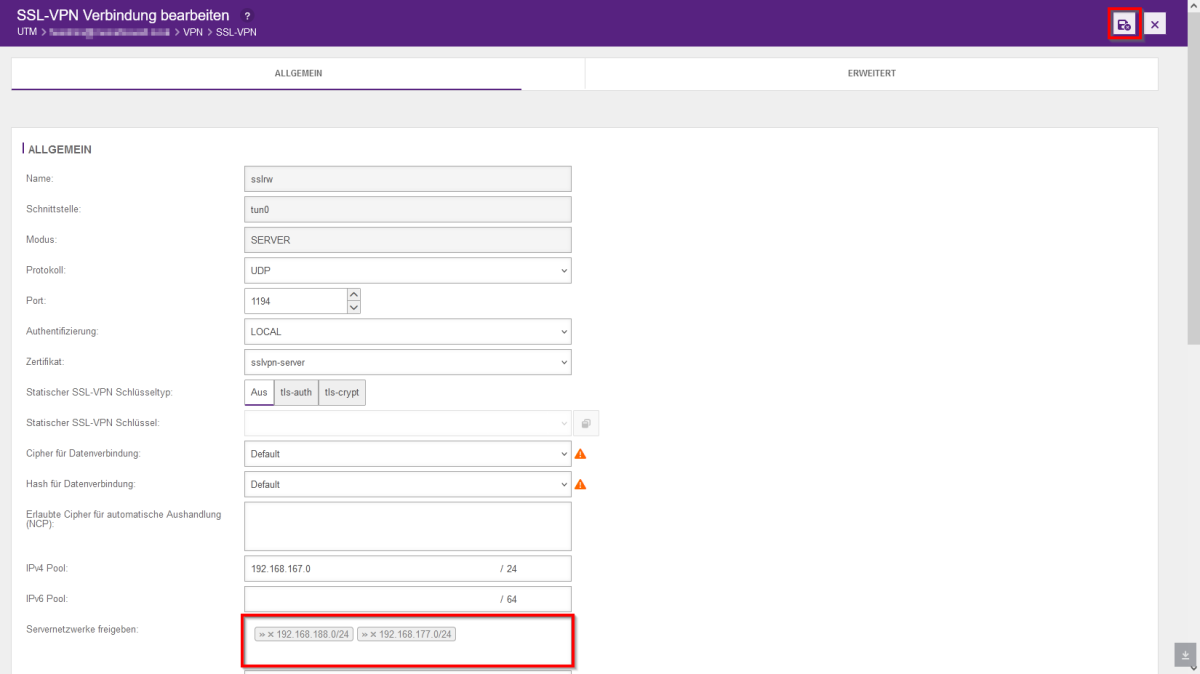
- Open the SSL-VPN configuration in the firewall web interface under the "VPN" tab.
- Click on the wrench on the right to edit the SSL-VPN connection.
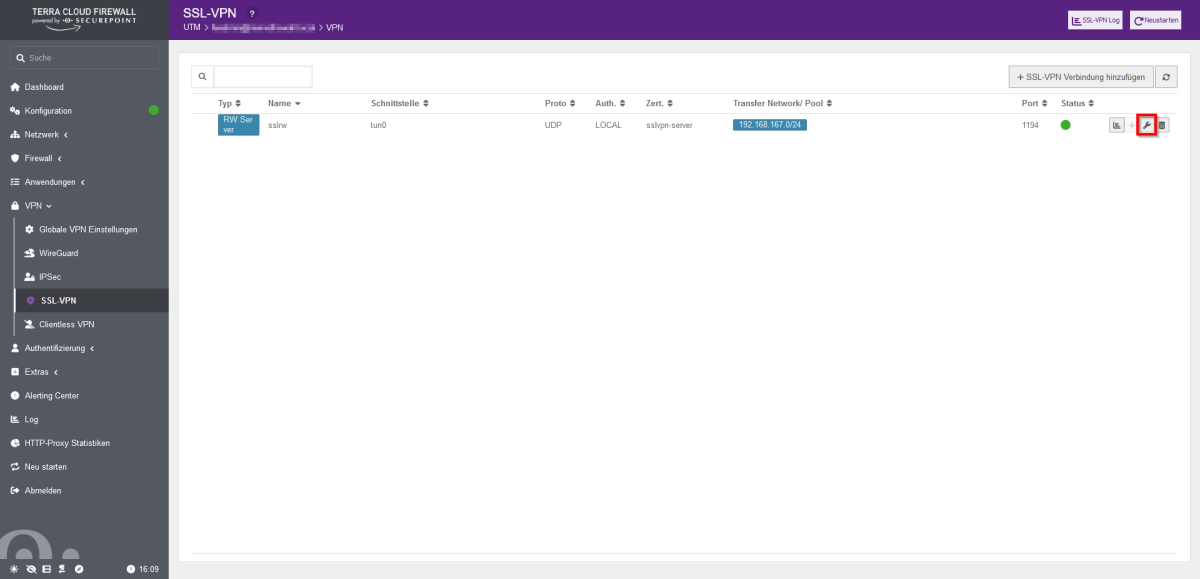
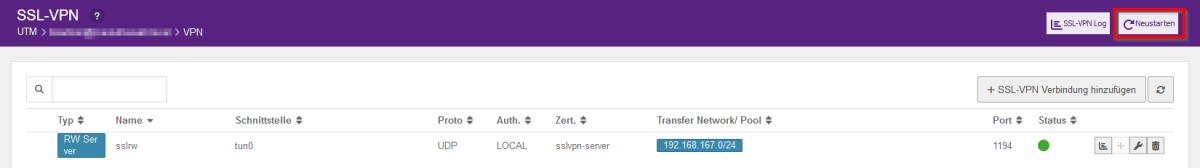
- You can then release the address range of the server networks. After adding, click on Save and then on "Restart".
- Please note that this will interrupt all tunnels and require a new tunnel to be set up!
- We then remove the old, no longer required network from the eth1 interface